Computer Networks Protocols
- Categories Computer Networks, Networking, Computer Networks
In this blog we will cover different network protocols which are used on communication over the internet.
There are billions of devices which are connected to internet which communicate with each other seamlessly.
In order for two computers to talk to each other, they must speak the same language. Internet needs to be very well planned and structured to enable this. That’s’ where network protocols come in.
Network Protocols are a set of rules governing exchange of information in an easy, reliable and secure way. These rules are the guidelines that regulate the different characteristics of a network, such as:
- different configurations,
- physical topologies,
- types of cabling,
- speed of data transfer
- access methods etc.
Why do we have so many protocols?
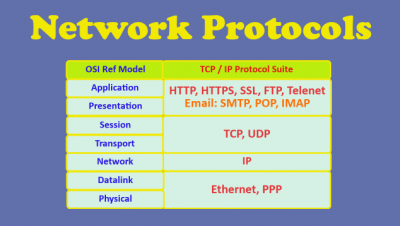
This is because when you talk of computer network, it is actually a layered architecture and is made up of multiple layers with each layer having its own set of protocols for communication within each layer. It then interfaces with layer above or below. We will not go into description of these layers but we will go over some popular protocols which are used across these layers.
Ethernet
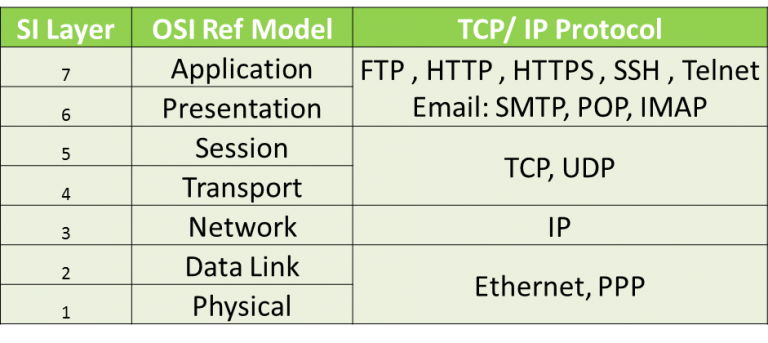
- Ethernet is a most important for LAN communication and It serves the physical and data link layers and provides the basic framework for data transmission.
- It divides a stream of data into shorter pieces called frames. These frames are encapsulated with destination address, error checking mechanism and other information.
- These frames are then sent over a media like coaxial cable. Ethernet transmits the data in digital packets.
- If any computer wants to use this protocol they should contain Ethernet Network Interface Card (NIC). The card is implemented with unique address code fixed in the microchip.
Point to Point Protocol or (PPP)
- Point to Point Protocol or (PPP) is a data link layer protocol that enables transmission of TCP/IP traffic over serial connection, like telephone line.
- It divides a stream of data into shorter pieces called frames.
- It defines the framing method to clearly define end of one frame and start of another, incorporating errors detection as well.
- It includes additional protocols for bringing communication lines up, authenticating and bringing them down when no longer needed.
Transmission Control Protocol/Internet Protocol.
- TCP/IP is actually a collection of protocols and is the current standard for communication used for both local and WAN which is the Internet.
- The communication model of this suite is client-server model.
- A computer that sends a request is the client and a computer to which the request is sent is the server.
Protocols it includes are TCP, UDP and IP:
IP is a connectionless network layer protocol responsible for providing addresses to each computer and performing routing. Currently Internet fully supports IPv4 and it is moving towards adopting latest version IPv6.
TCP is connection oriented Transport layer protocol which fragments messages into smaller packets and then sends them over the network. At receiving end the packets are reassembled in the correct order to restore the message again. It follows a standard handshake process with start and acknowledgement signals to establish connection.
UDP is connectionless protocol it allows packets to be sent without using handshake process. It is typically used to transfer small amount of information.
File Transfer Protocol (FTP)
- FTP or File Transfer Protocol is a standard for exchange of files across the net.
- It facilitates sharing of files between different computers or computer networks.
- It enables collaboration and use of remote computers.
- FTP is also the name of the program or command you issue along with the address of the site from where you want to transfer files.
- It works as a client/server process. It is one of the most used facilities on the internet.

HTTP or Hyper Text transfer protocol
- HTTP or Hyper Text transfer protocol is an application level protocol, designed for transferring a hypertext among two or more systems.
- It is a generic, stateless, object oriented protocol which can be used for many tasks.
- It is the basis for data communication for world wide web where we have documents or web pages with hyperlinks to other web pages or resources which a user can access with a mouse click.

- HTTP is designed on Client-server principles wherein client and web server engage in sequence of network request-response transactions called HTTP Sessions.
- A web browser, for example, may be the client and an application running on a computer hosting a website may be the server.
- HTTP has many built in request methods which allow a client system for establishing a connection with the server machine for making a request.

- The server acknowledges the request initiated by the client and responds accordingly.
- For e.g. The browser submits an HTTP request message to view a web page. The server, returns a response message to the client which includes requested content and status information.

Hypertext Transfer Protocol Secure (HTTPS)
- We now have an extension of the HTTP which is Hypertext Transfer Protocol Secure or HTTPS which is used for secure communication over a computer network.
- It is combination of HTTP and SSL/TLS protocols. HTTPS encrypts your data and establishes a secure channel over a non secure network.
- This ensures data is protected from eavesdroppers and hackers.
- It also authenticates the web server by checking whether it has a valid certificate by a trusted authority.
- You can validate this by making sure your URL starts with HTTPS and there is a lock sign on the navigation bar which shows the connection is secure.

SSL or secure Socet Layer
- SSL or secure Socet Layer provides security to the data that is transferred between web browser and server.
- SSL encrypt the link between a web server and a browser which ensures that all data passed between them remain private and free from attack.
- SSL is now deprecated as it is integrated with HTTPS.
- It requires that Website has SSL certificate installed to ensure its authenticity.
- The certificate is to be obtained by competent authority like GlobalSign.
- It is also indicated by lock sign on the browser navigation bar.

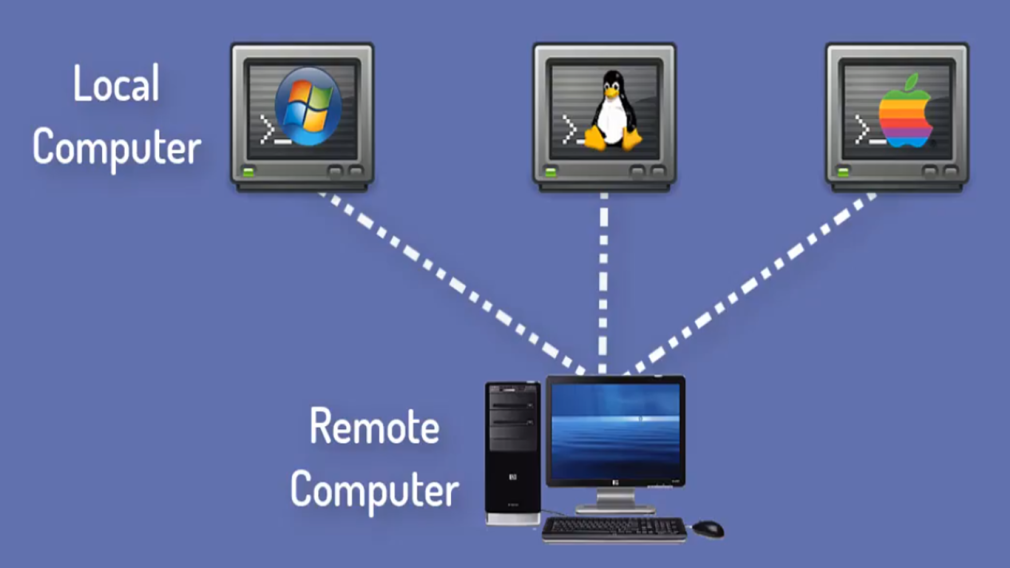
Telnet
- Telnet is used for remote terminal emulation.
- The connecting process here is termed as remote login.
- The system which requests for connection is the local computer, and the system which accepts the connection is the remote computer.
- It enables users to access remote computer applications by emulating one of the remote computer terminals.
- IT helps to provide connectivity between dissimilar operating systems.
- Telnet provides the services for remote operations of servers or using high configuration machines from dumb terminals.
Email Protocols
- Now we will cover various Email Protocols. The 3 protocols that we will cover are :
- POP
- IMAP
- SMTP
- Post Office Protocol Version 3 (POP3):
- POP3 or Post Office Protocol Version 3 is an application layer protocol used by email clients to retrieve email messages from mail servers over TCP/IP network.
- POP was designed to move the messages from server to local computer so that mails can be read even when they are not connected to the internet.
- POP3 is a very simple protocol to implement but that limits its usage.
- For example, POP3 supports only one mail server for each mailbox. It was used when internet connection was expensive.
- It has now has been made obsolete by modern protocols like IMAP.
- POP3 works on 2 ports.
- Port 110 – Default non encrypted port used for unsecured email communication
- Port 995 – Encrypted port used for secure email communication.
- IMAP stands for Internet Message Access Protocol:
- IMAP enabled email clients to retrieve email messages from mail servers over a TCP/IP connection.
- IMAP is designed to retrieve messages from multiple mail servers and consolidate them all in the user’s mailbox.
- A typical example is a corporate client handling multiple corporate accounts through a local mailbox located on her system.
- In addition to handling multiple mail boxes, IMAP has Faster response time than POP3 and can search for messages on the server and keep track of message state like read, deleted, starred, replied, etc.
- IMAP works on 2 ports.
- Port 143 – Default non encrypted port used for unsecured email communication
- Port 993 – Encrypted port used for secure email communication.
- SMTP stands for Simple Mail Transfer Protocol:
- It is connection oriented application layer protocol that is widely used to send and receive email messages between mail servers.
- However, user level applications use it only for sending messages.
- For retrieving they use IMAP or POP3 because they provide mail box management
- SMTP works on 2 ports.
- Port 25 – Default non encrypted port used for unsecured email communication
- Port 465 – Encrypted port used for secure email communication.
You may also like

Switching Techniques used in computer network

Communication Channels

